Framework
The ISMS Framework
Chief objective of Information Security Management is to implement the appropriate measurements in order to eliminate or minimize the impact that various security related threats and vulnerabilities might have on an organization. In doing so, Information Security Management will enable implementing the desirable qualitative characteristics of the services offered by the organization (i.e. availability of services, preservation of data confidentiality and integrity etc.).
It is not only size but in particular the specific business activities of an organization that dictate its security related requirements on a legal, regulatory and operational level.
Small businesses with limited information systems infrastructure, whose operation does not demand handling, storage and processing of personal or confidential data, usually face minor risks or risks with lower likelihood or impact. These organizations are more likely not to maintain independent ISMS and usually deal with information security risks ad-hoc or as part of a wider Risk Management process.
Larger organizations and organizations such as banks and financial institutes, telecommunication operators, hospital and health institutes and public or governmental bodies have many reasons for addressing information security very seriously. Legal and regulatory requirements which aim at protecting sensitive or personal data as well as general public security requirements impel them to devote the utmost attention and priority to information security risks.
Under these circumstances the development and implementation of a separate and independent management process namely an Information Security Management System is the one and only alternative.
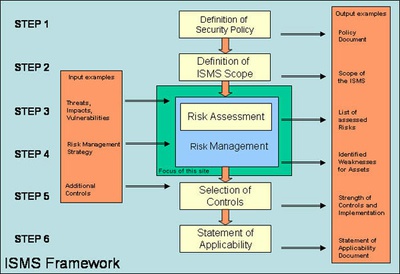
As shown in the figure above, the development of an ISMS framework entails the following 6 steps:
- Definition of Security Policy,
- Definition of ISMS Scope,
- Risk Assessment (as part of Risk Management),
- Risk Management,
- Selection of Appropriate Controls and
- Statement of Applicability
Steps 3 and 4, the Risk Assessment and Management process, comprise the heart of the ISMS and are the processes that “transform” on one hand the rules and guidelines of security policy and the targets; and on the other to transform objectives of ISMS into specific plans for the implementation of controls and mechanisms that aim at minimizing threats and vulnerabilities. It is worth mentioning, that steps 3 and 4 are considered as a single entity, namely Risk Management.
The processes and activities related to the steps 5 and 6 do not concern information risks. They are rather related to the operative actions required for the technical implementation, maintenance and control of security measurements.
Appropriate controls may either be derived from existing (exhaustive) sets of controls or mechanisms, usually included in information security standards (e.g. [ISO 17799]) and guidelines, or be the outcome of a combination or adaptation of proposed controls to the specific organizational requirements or operational characteristics.
In both cases, step 6 is the documented mapping of the identified risks, applied to the specific organization with the technical implementation of security mechanisms the organization has decided to deploy.
Finally it should be mentioned that although the ISMS is a recurring process as a whole, in most of the types of organizations mentioned above, steps 1 and 2 recur on a longer cycle than steps 3,4,5 and 6. This is mainly because the establishment of a security policy and the definition of the ISMS scope are more often management and (to a certain extent) strategic issues while the Risk Management process is in the end an “everyday” operational concern.