Assessment
Assess Risks and Impacts
Once the business critical processes of the organisation have been identified (see Section 337H8.2), the Business Continuity Manager may interview the managers of each business area at process level. The interview should ascertain for each process the impacts of losing technology or information in the following areas [BS 25999-1]:
- Impact on staff or public wellbeing
- Impact of breaches of statutory duties or regulatory requirements
- Damage to reputation
- Damage to financial viability
- Deterioration of product or service or service quality
- Environmental damage
HB 221:2004 adds the following impacts:
- Intellectual property, knowledge and data
- Stakeholder confidence and goodwill
- Political interest and comment
Additional methods to identify impact may be used. To this extent, qualitative or quantitative impact statements can be formulated. Such impact-measurement methods can be actually found in many Risk Management methods.
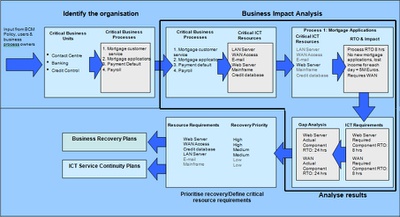
The technology required to operate each critical process should subsequently be identified and a Recovery Time Objective for that technology should be defined. This is the translation from process RTO (the RTO of the critical process as a whole) to component RTO (the RTO agreed for the various IT components required to operate the critical process itself). From the BIA data the ICT department must determine the supporting components. This may be a complex network as it may include several components (network, multiple servers, databases, data feeds from disparate systems, pre-requisite applications, security settings, web server, etc) or it may be simple (Finance departments typically have a standalone PC with a single application, modem and smartcard reader in order to authorise bank payments). ICT must list the components and recovery sequence.
It may be helpful at this stage to start with a list of known technology so the list is not being re-created when it already exists. The ICT department may already have this information on their asset list, or IS may have this information if they have recently conducted a Risk Assessment. If this information is not already held, it would be a good idea to co-ordinate the efforts of ICT and IS. In this way, that not only are the details for the BIA collected, but any other information the ICT or IS departments may wish to gather about the business areas’ use of technology and information are also obtained.
ICT will then be in a position to map the recovery process for components and relate the combined component RTO to the process RTO. If the sum of the components cannot be recovered within the process RTO then there is a gap.
For a BIA the minimum information which the Business Continuity Manager needs to gather from the business process manager is:
- business area and process names
- Recovery Time Objective for the process (based on the criticality ratings and recovery timescales defined in the BCM Policy)
- type of software used
- acceptable levels of downtime for the software
- information required (electronic and paper)
- acceptable levels of downtime for the information
- type of hardware used (can include workstations, printers, faxes, exception PCs, modems etc...)
- number of items of each hardware type normally used
- minimum number of items of each hardware type which could be used during an incident
- acceptable levels of downtime for the hardware
- telephony used
- acceptable levels of downtime for the telephony
- Service Levels agreed with hardware, software and service providers and within any IT support contract
The BIA should also be carried out on ICT and IS as an incident may require them to operate from an alternative location, and it is essential that they understand how they will support the organisation should they be affected by an incident.
If it has not already been carried out as part of the organisation’s Risk Management, a Risk Assessment should be carried out on ICT and IS to assess areas of risk that may lead to a disruption. This Risk Assessment should be carried out in accordance with any of the relevant Risk Management methods as the ones described [ENISA RM].
The outcome of the Risk Assessment will provide the information with which to assess ICT and IS’ vulnerabilities and allow them to develop an action plan to mitigate the risks. It is likely that some of the risks cannot be eliminated and the Business Continuity Plan must address them and provide a course of action should a disruption occur.