Overview of the Methodology
The assessment of risks is the first step towards the adoption of
appropriate security measures for the protection of personal data.
In this section, we present an overview of the approach that was
proposed by ENISA in 2017 towards guiding the SMEs through their
specific data processing operation and supporting them in evaluating
relevant security risks. As such, the proposed approach does not
present a new risk assessment methodology but rather builds on existing
work in the field to provide guidance to SMEs.
This approach is based on the five step approach, depicted in Figure 1 below.
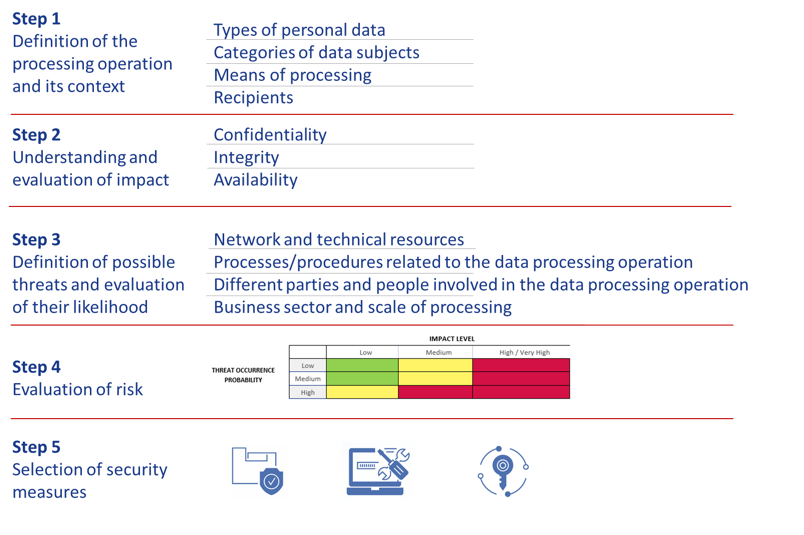 Figure 1: Overview of proposed approach on evaluating the risk on
personal data processing
Figure 1: Overview of proposed approach on evaluating the risk on
personal data processing
Hereinafter, follows a brief overview of the aforementioned methodological steps. A more detailed analysis of each step is included in “ Guidelines for SMEs on the security of personal data processing”.
Step 1: Definition of the processing operation and its context
This step is the starting point of the risk assessment and is fundamental for the data controller/processor in order to define the boundaries of the data processing system (under assessment) and its relevant context. In doing so, the organization needs to consider the different phases of data processing (collection, storage, use, transfer, disposal, etc.) along with relevant aspects such as data recipients, means used for processing etc.
The following questions need, as a minimum, to be asked and to be clearly understood by the data controller/processor. Relevant examples and practical guidance, through use cases, can be found in [ENISA, Handbook, 2018].
- What is the personal data processing operation?
- What are the types of personal data processed?
- What is the purpose of the processing?
- What are the means used for the processing of personal data?
- Where does the processing of personal data take place?
- Which are the categories of data subjects?
- Which are the recipients of the data?
Step 2: Understanding and evaluating the impact
In this step, the data controller/processor is guided to evaluate the potential impact to the rights and freedoms of individuals that a security incident (related to the data processing system) might bring. The security incident may be associated to any type of breach of confidentiality, integrity or availability of personal data.
Due to the ad-hoc nature and diversity of personal data processing operations, only a qualitative approach can be used, based on the overall understanding (by the organization) of its specific data processing operation. To this end, the evaluation of the impact is based on a number of parameters, such as the type and volume of personal data, the criticality of the processing operation, special characteristics of the data controller/processor, special characteristics of the data subjects, as well as the level of identifiability of data subjects. Following this assessment, the controller is finally asked to assess the impact, based on four predefined levels, i.e. low, medium, high and very high (see Table 1).
| LEVEL OF IMPACT | DESCRIPTION |
|---|---|
| Low | Individuals may encounter a few minor inconveniences, which they will overcome without any problem (time spent re-entering information, annoyances, irritations, etc.). |
| Medium | Individuals may encounter significant inconveniences, which they will be able to overcome despite a few difficulties (extra costs, denial of access to business services, fear, lack of understanding, stress, minor physical ailments, etc.). |
| High | Individuals may encounter significant consequences, which they should be able to overcome albeit with serious difficulties (misappropriation of funds, blacklisting by financial institutions, property damage, loss of employment, subpoena, worsening of health, etc.). |
| Very high | Individuals may encounter significant or even irreversible consequences, which they may not overcome (inability to work, long-term psychological or physical ailments, death, etc.). |
The total impact is assessed separately for the loss of confidentiality, integrity and availability. The highest of these levels is then considered as the final result of the evaluation of the impact, relating to the overall processing of personal data.
Step 3: Definition of possible threats and evaluation of their likelihood
A threat is any circumstance or event, which has the potential to adversely affect the security of personal data. At this step, the goal for the data controller/processor is to understand the threats related to the overall environment of the personal data processing (external or internal) and assess their likelihood (threat occurrence probability). Varying levels and types of threats to the confidentiality, integrity and availability of personal data could be considered in this respect.
Similar to the case of the evaluation of impact, the assessment of threat occurrence probability can only be qualitative, as it is very much related to the specific personal data processing environment. In the context of ENISA’s approach, three levels of threat occurrence probability are defined, namely:
- Low: the threat is unlikely to materialize.
- Medium: it is possible that the threat materializes.
- High: the threat is likely to materialize.
To simplify the process for SMEs, the ENISA’s approach defines four areas of assessment for threat occurrence probability and guides the controller through them, namely:
- Network and technical resources (hardware and software
- Processes/procedures related to the data processing operation
- Different parties and people involved in the processing operation
- Business sector and scale of the processing
Step 4: Evaluation of risk
After evaluating the impact of the personal data processing operation and the relevant threat occurrence probability, the final evaluation of risk is possible, as shown in Figure 2 and Table 2 below.
 Figure 2: Final risk evaluation
Figure 2: Final risk evaluation
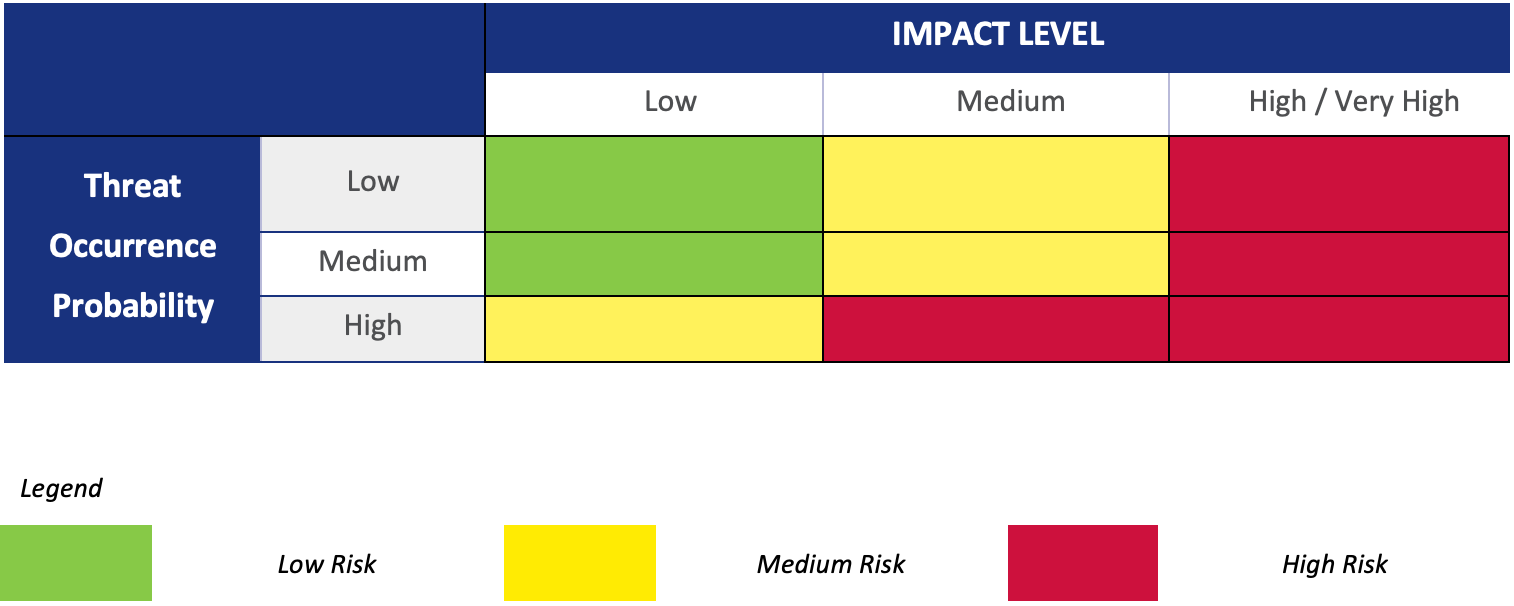 Table 2: Evaluation of risk
Table 2: Evaluation of risk
Regardless of the final result of this exercise, the data controller/processor retains the discretion to adjust the obtained level of risk level, taking into account specific characteristics of the data processing operation (that have been missed during the assessment process) and providing adequate justification for this adjustment.
Step 5: Selection of appropriate security measures
Following the evaluation of the risk level, the data controller/processor can proceed with the selection of appropriate security measures for the protection of personal data. Two broad categories of measures, organizational and technical ones, which are further divided in specific categories, are considered (Table 3). In principle, they follow the categorization given in ISO/IEC 27001 Annex A and ISO/IEC 27002.
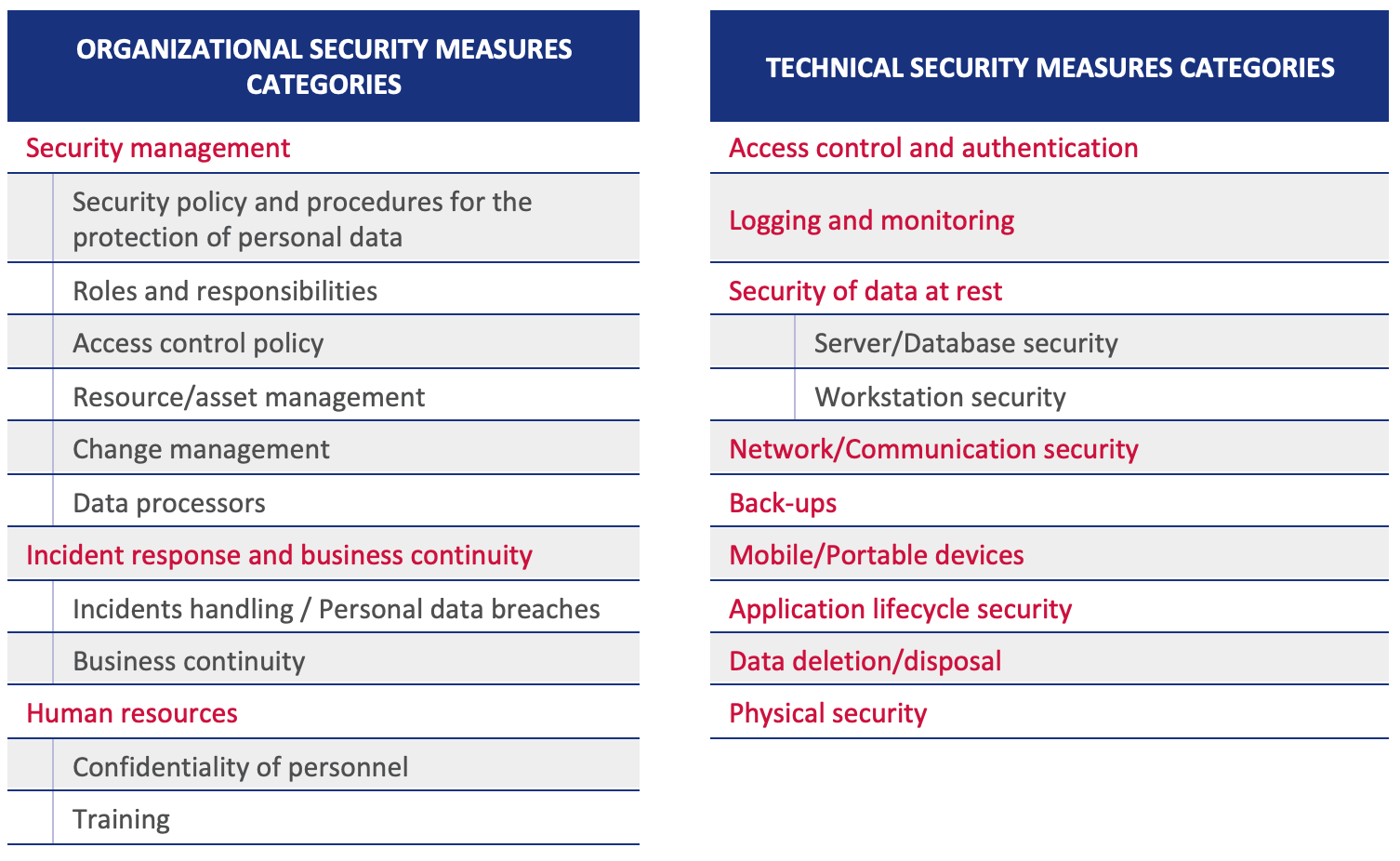 Table 3: Overview of categories of security measures
Table 3: Overview of categories of security measures
Under each category, the measures are further presented per risk level (low: green, medium: yellow, high: red). In order to achieve scalability, it is assumed that all measures described under the low level (green) are applicable to all levels. Similarly, measures presented under the medium level (yellow) are applicable also to the high level of risk. Measures presented under the high level (red) are not applicable to any other level of risk.
Depending on the context of the personal data processing, the organization can consider adopting additional measures, even if they are assigned to a higher level of risk. Furthermore, the proposed list of measures does not take into account other additional sector specific security requirements, as well as specific regulatory obligations, arising for example from the ePrivacy Directive, the NIS Directive, the Payment services Directive (PSD 2) etc.