Time for security policy review
This note provides an overview on how digital transformation and sophistication of threats may turn common security policies obsolete;
- Published
- February 26, 2018
Introduction
The use of personal mobile devices is omnipresent in daily life, expanding significantly the options for new applications and services. A wide range of applications using such devices implement a broad spectrum of functions and capabilities that are relevant in both the personal and professional spaces. This development is also referred to as “digital transformation”. Such applications and services introduce new user behavior with regard to managing and sharing sensitive information, both personal and professional. Furthermore, with digital transformation, mobile devices became a more attractive target to an increasing and more sophisticated number of threats.
Numerous incidents encountered recently have demonstrated the severe impact to organization’s security resulting in the materialization of risks related to digital transformation. “Strava Heat Map”, “Android security triple-whammy attack” and “SideStepper attack against Apple MDM” are just a few examples.
This note provides an overview on how digital transformation and sophistication of threats may turn common security policies obsolete; and it will increase the exposure to new risks, others from the ones that have been initially assessed.
Contextual Information
As employees become more reliant on mobile devices, exposure to new cyberthreats pose an even greater challenge on organizations to review security policies. CISOs traditionally focus on operated personal smartphones, laptops and tablets, with consumerization of IT the spectrum of devices and gadgets brought into the workspace widens.
Risk of Unintentionally Exposure of Sensitive Information
New type of devices such as Wearables are invading the workplace in much the same way smartphones did till now. Fitness trackers, smartwatches, wristbands and action cameras are examples of devices employees are introducing into the workspace. They are usually connected either to the smart phone and/or with the internet/web.
The recent Strava incident exposed weaknesses in the use of wearable devices by soldiers in restricted areas while on duty. The incident involved a fitness tracking company preparing a heat map with customer’s geolocation data from smartphones, trackers and smartwatches using satellite imagery, published on the internet. This example demonstrates how gadgets may violate security policies protecting the secrecy of location: geolocation data captured by an application and transmitted over the internet. Hence, the requirement of a secret location could not be fulfilled, lading thus to a breach of the corresponding security policy.
New Application Functions and Services Exposing Vulnerabilities
The fast growing market of mobile applications encourage consumers to install and subscribe services for personal or professional use without evaluating potential risks. When an application processes sensitive information taken as input from corporate sources, it may result in placing that data in an insecure (unencrypted) location in the device. This insecure location could be accessible to other malicious applications running on the same device, identified as side channel data leakage, thus leaving the device in a serious risk state. Organization’s sensitive data stored in mobile devices running vulnerable applications become an easy target for attackers to steal information in undetectable way.
Highly Sophistication of Malware for Mobile Devices
During the last quarter of 2017, a security researcher discovered and disclosed a new piece of highly sophisticated Malware identified as Skygofree targeting Android devices. According to the researcher, this malware is able to monitor user activity, record audio, intercept WhatsApp messages and connect the device to any Wi-Fi network without the user knowledge. “Bad actors have the ability to control the implant via HTTP, XMPP, binary SMS and FirebaseCloudMessaging protocols.” stated the researcher. Hence, the availability of such functions shed a new light to security policies disallowing the use of mobile devices by visitors to prevent leakages. Such incidents may be caused at a higher level of efficiency by manipulating smart phones of employees. In particular, by using geo-fencing functions the misuse can be performed in a more targeted manner.
List of some known vulnerabilities within mobile interconnected devices and services:
- Inexistent or poor encryption of some mobile devices and applications to store and transmit data;
- Unintended data leakage or side-channel data from mobile applications stored in mobile devices;
- Personal mobile devices often do not fall under MDM (Mobile device management) controls and policies such as automatic installation of updates, restriction in the installation of unsecure applications and installation of security software;
- Insecure data storage of sensitive and confidential information from corporate emails and cloud services accessed from mobile devices;
Sensitive data captured and shared by devices such as geo-location, images of security restricted areas and audio recordings;
Threat Mapping:
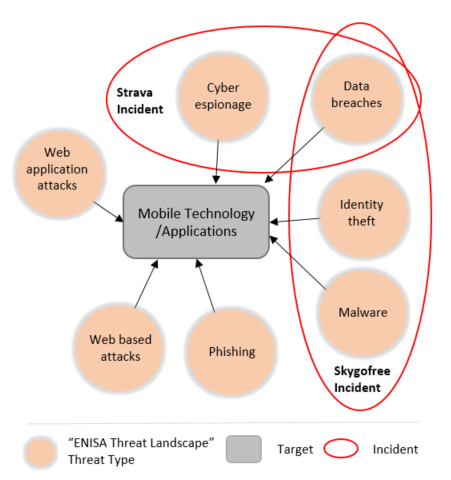
Figure 1 - Map for Strava heat map and Skygofree threats
Recommendations
For many organizations, security policies regulating the use of personal mobile technology in the workplace require a significant revision in a timely manner. In the past, such policies have been subject of BYOD (Bring Your Own Device) policies/implementations. In most cases – even within existing BYOD policies - the line between corporate and personal is not clearly defined. Technical mobile devices vulnerabilities, but also weaknesses/errors associated to user behavior can easily compromise security policies and place corporate data at risk. Therefore, the onus is on organizations to assure that existing security policies address the latest security concerns and take into account possible weaknesses introduced by (the use of ) emerging technologies.
Topics to consider when reviewing security policies regulating the use of personal mobile technology:
- Eligibility of employees that can benefit from the use of personal mobile devices in the workplace;
- Use of personal mobile devices in the workplace conditional to the inclusion in MDM system;
- Define restricted areas where personal mobile devices are not allowed;
- Determine the type of devices that can be used in the workplace;
- Define boundaries between corporate and personal information;
- Promote regular employee education and change management;
- Review the rules for corporate information disclosure;
Closing Remarks
Organization’s exposure to mobile devices threats continues to grow as technology evolves. The introduction of mobile technology for personal or professional use in the workspace poses a variety of challenges to IT and security managers in general. The growth in number and sophistication of threats affecting mobile devices and their ecosystem requires an urgent revision of security policies and regulations. Revision that should not only focus in technology but also user behaviour through the investment in change management, training and awareness programs.