Ransom attacks against unprotected Internet exposed databases
In late August 2017 to early September 2017, security researchers detected a new wave of ransom attacks against MongoDB databases.
- Published
- September 13, 2017
Introduction
In late August to early September 2017 ransom attacks against MongoDB databases re-emerged. Three new threat actors hijacked over 26,000 MongoDB databases. The re-surfaced attacks came several months after similar attacks peaked during late 2016 to early 2017, affecting 45,000 MongoDB databases. This note provides an overview of past and new incidents, identifies the cyber-threats related to these attacks, provides security recommendations, and highlights the importance of properly securing any Internet accessible service.
Attacks against Internet exposed services
In late 2016, a security researcher, identified attacks against Internet exposed and unprotected MongoDB instances. Initially, about 2,000 databases were reported as being compromised. In early January 2017, such compromises skyrocketed from 12,000 to 27,000 within a single day. More recent reports mentioned that compromises escalated to 45,000 within a month. This is a significant number of databases exposed on the Internet without proper authentication mechanisms in place, left open to attacks.
Attacker(s) massively scanned the Internet and hijacked unprotected Internet exposed MongoDB databases. They essentially kept a copy of the databases (although not in all cases), deleted the databases from the victim systems, and replaced them with a ransom note asking for 0.2 Bitcoins in exchange for restoring the databases.
Shortly after the first MongoDB ransom attacks, attackers turned their attention to other Internet exposed and unprotected services as well. Attacks against Amazon’s exposed ElasticSearch servers , Apache CouchDB, and Hadoop Distributed File System installations followed a similar ransom tactic. Although, in most of these cases data was deleted straight away without any ransom request.
New wave of attacks
In late August 2017 to early September 2017, security researchers detected a new wave of ransom attacks against MongoDB databases. In this case the affected databases were also left exposed on the Internet allowing external un-authenticated access. Three new threat actors hijacked over 26,000 databases and replaced their content with a ransom note. The ransom demanded from 0.05 Bitcoins (approximately €190 at the time of writing) to 0.2 Bitcoins (approximately €750 at the time of writing). It is under investigation why the attacks had such an impact, several months after the first incidents.
Cyber-threat context in ransom attacks & recommendations
The following figure illustrates the steps involved in the MongoDB ransom attack, the cyber-threats related to it and the potential threat agents identified. The ransom attack involves cyber-threats that have been described in ENISA’s Threat Landscape (Web-based Attacks, Data Breaches, and Ransomware).
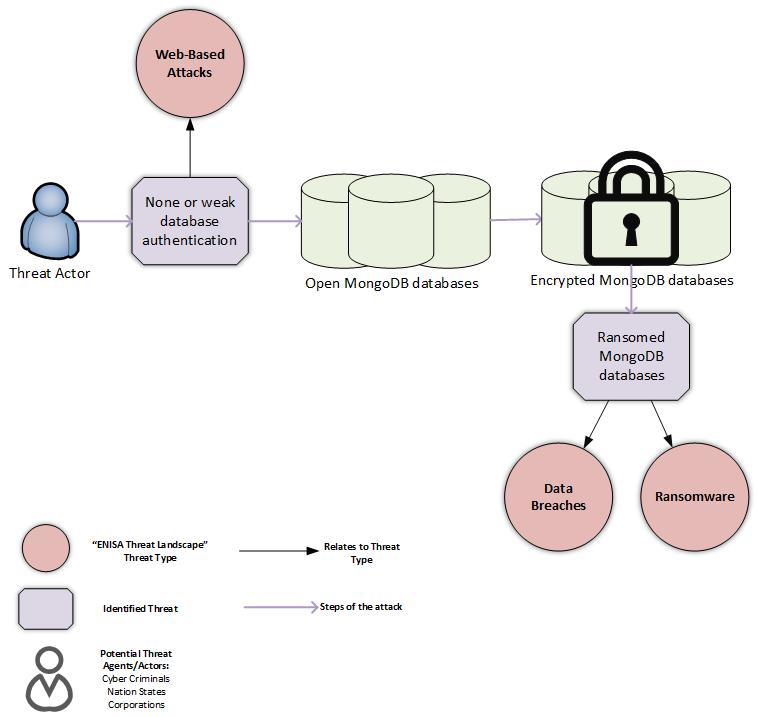
Identifying the cyber-threats involved in this ransom attack, provides a reference point to ENISA’s Threat Landscape for more security recommendations. Some recommendations for the MongoDB database compromises, which can be applied to other Internet exposed services as well, are the following -arranged according to the identified threat types:
- Any Internet-exposed service must be properly configured and secured in advance. Default service configuration can potentially allow un-authentication access to the service. This is a crucial security measure that should not be overlooked. (related threat type: Web-based Attacks)
- Maintainers of services should re-assess their default configurations and make sure they provide hardened default configurations for their services before they are widely deployed. After the latest attacks MongoDB is also working towards that direction as well. (related threat type: Web-based Attacks)
- Use strong and unique passwords (as well as two-factor authentication when available) for all accounts of a service/database and prevent users from accessing the administrative interface from the Internet if not absolutely necessary. (related threat type: Web-based Attacks)
- MongoDB security is addressed in the official security manual. Database and system administrators need to carefully configure their databases before exposing them online. The same applies for other Internet exposed databases/services as well, and their respective manual should be consulted in order to configure them properly. (related threat type: Web-based Attacks)
- Proactively back-up MongoDB databases and other critical system data to quickly restore operation after a compromise, without paying the ransom. (related threat type: Ransomware)
- Be compliant to personal data protection regulations, i.e. EU data protection legal framework and in particular the new GDPR entering into force in May 2018. (related threat type: Data Breaches)
Conclusion
In 2016, ransomware was a dominant cyber threat and affected various sectors, e.g. academic institutions, hospitals, government bodies, industry etc. In 2017, ransomware further evolved by enhancing its malicious tactics, e.g. using worm-like capabilities. Ransomware’s success underscored, in the most prominent way, the monetization of cybercrime. Ransom attacks against Internet exposed services are a trend, which fits that pattern and deepens the abuse caused by threat actors. Again, such incidents prove that following best practices, e.g. properly securing Internet exposed services, is crucial, and should be followed at all times.