Mailsploit – E-mail spoofing and code injection vulnerabilities
Mailsploit refers to a series of bugs found in e-mail clients that allow a potential attacker to spoof the e-mail sender address (i.e. identity spoofing) and in certain cases even perform code injection attacks.
- Published
- December 13, 2017
Introduction
A security researcher discovered a set of vulnerabilities, collectively dubbed “Mailsploit”. As the name suggests, Mailsploit refers to a series of bugs found in e-mail clients that allow a potential attacker to spoof the e-mail sender address (i.e. identity spoofing) and in certain cases even perform code injection attacks. Identity spoofing is very dangerous because it significantly enhances the efficiency of phishing/spear-phishing attacks, the most used vectors for delivering malware/ransomware and stealing personal data. This note provides an overview of the issue, puts Mailsploit into the context of the general threat landscape, and provides security recommendations for mitigating risks related to Mailsploit.
Mailsploit overview
Mailsploit allows a threat agent to spoof the sender address of an e-mail and consequently impersonate someone else by displaying a sender address of their choice to the recipient/target. This activity is also known as identity spoofing and, to a certain extent, is a form of identity theft. For example, by leveraging Mailsploit, someone with the registered e-mail address “[email protected]” could send an e-mail appearing as “[email protected]”.
According to the researcher who discovered Mailsploit, all e-mail headers including the “From” e-mail header, must only contain ASCII characters. On this basis, in 1992 the RFC-1342 standard was adopted in order to automatically convert non-ASCII characters to ASCII characters and avoid errors when e-mails with non-ASCII characters in e-mail headers were processed by different mail servers. Mailsploit takes advantage of the standard RFC-1342. It uses it to encode non-ASCII characters and manipulate the “From” e-mail header. Hence, a carefully crafted string can be used in the “From” e-mail header, leading to identity spoofing and in some cases to code injection. What makes the attack possible, is the fact that e-mail clients and web interfaces do not properly sanitise the string in the “From” header after they decode it. This is a severe omission: in web interfaces and application APIs, non-validated (user) entries are the main cause of code injection.
Some of the e-mail clients that were found vulnerable to e-mail spoofing attacks, were also found vulnerable to code injection attacks. More specifically it was possible to inject malicious code in the “From” e-mail header and perform cross-site-scripting (XSS) attacks. This attack vector does not apply to all e-mail applications that were found vulnerable to Mailsploit.
Mailsploit can effectively bypass existing anti-spoofing protection mechanisms (DKIM/DMARC) and spam filters, and has been spotted in over 30 e-mail applications like Apple Mail, Mozilla Thunderbird, Yahoo! Mail, ProtonMail etc. Some companies have already addressed the issue, while others are working on a fix, and a few are not expected to provide a fix for their software at all, as they consider it a server-side issue.
The researcher who discovered Mailsploit has created a dedicated webpage describing the vulnerabilities and has also provided videos with proof of concepts of the attack.
Mailsploit and cyber threat contextual information
Mailsploit is an ideal candidate for phishing and spear-phishing campaigns and by extension for delivering malware, ransomware and stealing personal data. The identity spoofing attack is essentially an identity theft threat as described in ENISA’s Threat Landscape - ETL. Finally, the code injection attack vector of Mailsploit is related to “Web application attacks” as they are also described in ETL. The figure below illustrates the connection of Mailsploit with the aforementioned and well documented cyber threats. This information is useful because it puts Mailsploit in the context of the general threat landscape and allows readers to seek for specific security recommendations for each identified threat, in ETL.
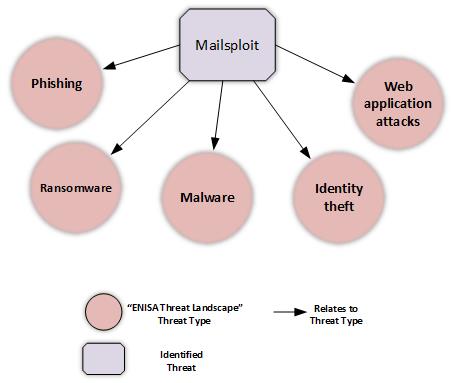
Figure 1: Mailsploit threat context.
Recommendations
Below you can find the main recommendations for protecting against Mailsploit:
- Update your e-mail client or operating system as soon as a software update is available.
- Use PGP/GPG to verify the identities of the people you exchange e-mail with and encrypt e-mail contents.
- Advanced users that have suspicions of a potentially fraudulent e-mail can check the full e-mail headers for anomalies (in their e-mail client). For example a legitimate “From” e-mail header looks like: “From: [email protected]”. A fraudulent “From” e-mail header appearing as ”[email protected]” would look like: ‘From: "=?utf-8?b?am9lQGRvZS5jb20=?=" [email protected]’ instead.
- Consider alternative software solutions for communication, such as private messengers that use end-to-end encryption and have provisions for identity verification.
- Consult ETL for more recommendations in relation to the identified threat types (see Figure 1).
Closing remarks
Mailsploit essentially exploits the inherent trust of users to e-mail. It is almost impossible for ordinary users to spot an attack that leverages Mailsploit. This makes it a serious threat and a stepping stone for further attacks. Awareness is key and users should be vigilant for attacks using Mailsploit.