Is Software More Vulnerable Today?
This note provides an overview on the reasons for the growing number of disclosed vulnerabilities and the impact it has in the industry credibility and confidence in the technology market.
- Published
- March 12, 2018
Introduction
It has been recurrent for hardware and software vendors to issue regular updates patching software flaws and vulnerabilities. Over the years, vulnerabilities have almost constantly increased reaching a peak in 2017 with the number reported more than doubling the previous year. This development seems to continue in the current year. In the realm of this trend, one may raise the question: Is today’s software more vulnerable?
This note provides an overview on the reasons for the growing number of disclosed vulnerabilities and the impact it has in the industry credibility and confidence in the technology market.
Contextual Information
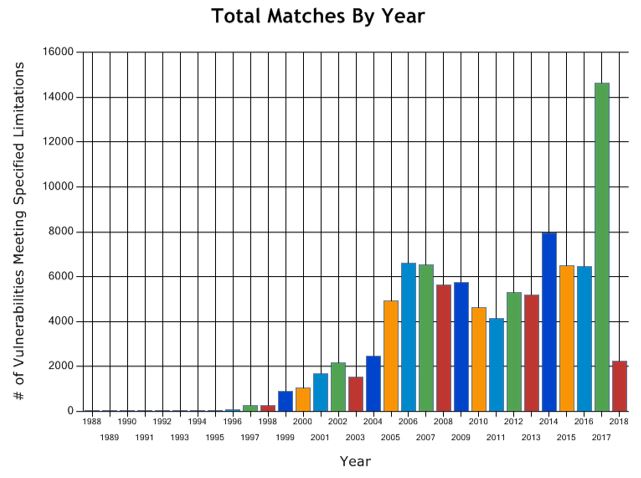
According to two US based organizations that track vulnerability disclosure, the number of software vulnerabilities has gradually grown year-over-year achieving its highest peak in 2017. Both National Vulnerability Database (NVD) maintained by NIST and Common Vulnerability and Exposures (CVE) database maintain by Mitre, recorded over 14,500 new vulnerabilities in 2017 compared with 6,000 from previous year. Yet in 2018, 2,000 new vulnerabilities reported during the first two months match the number observed during the entire year of 2002. Maintaining this trend a new record could be set this year reaching the 24,000 disclosures almost doubling those of 2017.
Last year's WannaCry and NotPetya aggressive outbreaks were caused by the disclosure of EternalBlue zero-day. Meltdown and Spectrum vulnerabilities have illustrated how important it is for the industry to rapidly react and release patches to fix disclosed flaws. Indicative to this trend are the recent software updates issued by major industry vendors fixing critical security vulnerabilities. In the first two months of 2018 only, four major vendors have issued updates to patch 348 security issues:
- Adobe Acrobat Reader APSB18-02 - February 13, 2018. – Correcting 41 security issues;
- Windows security updates released January-February, 2018, and antivirus software – February 13, 2018 – Correcting 51 security issues;
- MacOS High Sierra 10.13.3, Security Update 2018-001 Sierra, and Security Update 2018-001 El Capitan. – Correcting 18 security issues;
- Oracle Critical Patch Update Advisory - January 2018. – Correcting 238 security issues and;
- Google patched 45 vulnerabilities in Chrome 65 - March 2018 - Correcting 45 security issues.
For decades, the industry promoted the idea that hard- and software cannot be completely error and vulnerability free given the fact that these are complex systems designed and developed by people. Vendors use disclaimers and lengthy end-user license agreements (EULA), that consumers rarely read, to excuse and exempt themselves from any responsibility or damage caused from the use of their products. Nevertheless, consumers’ appetite for innovation still holds a reasonable degree of tolerance to accept that in early versions, products are released with vulnerabilities and errors. It is evident however, that early-adopter posture may eventually decline, given the fact that attacks follow the same trends as critical vulnerabilities: successful impactful attacks are proportional to the number and severity/criticality of vulnerabilities.
Reason for the Growing Number of Disclosed Vulnerabilities
Different reasons explain the growing number of disclosed vulnerabilities.
- Disruptive innovation and the continuously evolving technology landscape enable the deployment of growing number of new technology products and services. The commercial successes of mobile devices, cloud computing, social media, mobile applications, Internet-of-Things (IoT) – for example – opened opportunities for innovative businesses, albeit with relatively low maturity in software development and secure-coding skills.
- Innovation and strong competition in the technology space leads to more hard- and software products. The demand for shorter time-to-market is pressing vendors to releases products faster and reduce the resources required for quality assurance and testing.
- Modern software applications are increasingly complex due to the demand for interconnectivity, integration and platform compatibility. In fact, 80% to 90% of modern applications are built using open-source software components. This trend increases likelihood for the existence of vulnerabilities. Recent research has estimated that 1 in 18 open source components downloaded in 2017 had a known security vulnerability.
- The number of vendor-independent people and organizations involved in research and discovery of vulnerabilities is increasing. According to a recent study, this group is considered the largest contributor for the growing number of vulnerabilities disclosed. Bug bounty / research reward programs promoted by major industry vendors are intended to mobilize this group into testing the products in exchange of a reward. Examples of Google Vulnerability Reward Program (VRP) and Microsoft Security Research Centre recognize the value of this work.
- With cyber-crime becoming a profitable activity, the increasing number of threat actors is also involved in vulnerability research. A significant number of vulnerabilities is attributed to cyber criminals looking for new tools to support their attacks.
- With Cyber Security on top of the agenda, nation-states are also actively engaged in vulnerability research to support lawful interventions in IT-systems. Media reports on Nation States seeking for new vulnerabilities have been recently published.
- Vulnerability-by-design implemented by vendors leave backdoors in the software with the aim to explore them for various reasons: malicious purposes, hidden commercial agendas or surveillance programs. In 2015, the media reported that a Nation State has adopted new regulation requiring the inclusion of back-doors in hard- and software.
- Outdated system architectures that, for different reasons, are still in use and can be found in released products. Meltdown and Spectre are recently disclosed vulnerabilities that affected a big variety of microprocessor released since 1995 until today. ENISA recently published an Info Note describing these vulnerabilities.
- Without adequate legislation and regulation, to protect consumer rights with software defects and vulnerabilities, there is no incentive for the industry to invest in more secure products and assume liability for damages caused.
Impact for Consumers and Market
The impact of vulnerabilities for consumers is vast, though the future introduction of General Data Protection Regulation (GDPR) creates a sense of urgency for organizations to review and evaluate the impact of software vulnerabilities with regard to data protection. Article 32 of the GDPR states that organizations must “implement appropriate technical and organizational measures” to “ensure the ongoing confidentiality, integrity, availability and resilience of processing systems and services.” When combined with Article 25, which mandates that data protection measures be implemented “by design and by default”, it is clear that failing to follow these rules, due to inadvertently share of data from vulnerabilities exploitation, may have considerable reputational and financial impact for organizations. Impact for organizations that hold the data but also for software vendors responsible for the development and implementation of the systems.
The recent incident with Equifax, a US based agency specialized in consumer credit reporting, represents one of the most notorious heist in the history of data breaches. It took three days for attackers to drain 145 million records from Equifax database, taking advantage of a known security vulnerability in the Apache Struts2 open source software component.
Mitigation
While for the majority of vulnerabilities disclosed in 2017 (ca. 72%) there is a patch or update available, for ca. 23% there is no known fix available. Vulnerabilities cause a significant risk exposure whose reduction can be achieved through coordinated action by different stakeholders. Below we address important activities to be performed per stakeholder group:
From an end-user perspective:
- Maintain an up-to-date inventory of digital assets and connected devices;
- Perform a regular review of security and privacy policies;
- Conduct regular software patching and updating;
- Implement automated security vulnerability scanners and;
- Leverage from vulnerability reporting databases.
From a vendor perspective:
- Adopt a security-by-design approach during the entire product development life-cycle;
- Invest in the recruitment/development of secure-coding skills;
- Introduce AI more specifically machine learning to automate product development testing cycles;
- Implement personal data protection systems and processes in accordance with data protection law;
- Allow consumers to delete their own personal data on devices and products;
- Make sure that credentials are securely stored within services and on devices and that hard-coded credentials are not used;
- Promote and incentive collaborative and responsible vulnerability disclosure in partnership with the various industry players and the security research community and;
- Respond to vulnerabilities reports in a timely manner. Implement vulnerability management systems and processes.
From a research community perspective:
- Adhere to responsible vulnerability disclosure in partnership with the industry and the research community;
- Facilitate the improvement of vendor maturity and;
- Setup infrastructures to coordinate the registration and maintenance of vulnerabilities.
From a policy maker perspective:
- Develop policies that subject the industry to software product liability laws and protect consumer rights;
- Develop a legal landscape to address the challenges faced by the different stakeholders involved in the vulnerability research and disclosure process and;
- Promote education in cyber security.
In January 2016, ENISA published a comprehensive study on vulnerability disclosure taking stock of the situation, identifying the challenges and good practices and, propose recommendations. The Center for European Policy Studies (CEPS), an EU think tank, is also an active contributor to the vulnerability disclosure discussion. The organization recently promoted an EU Parliament roundtable to discuss guidelines to harmonize the process of Coordinated Vulnerability Disclosure (CVD).
Closing Remarks
Concerns with software defects and vulnerabilities is not new and increases as economy and society become more reliant on technology. The considerable growth of vulnerabilities over the years is caused by: innovative and evolving market, low maturity in products, organizations and skills to name a few. Now, more than ever, it is urgent that all stakeholders contribute to invert this trend. The introduction of General Data Protection Regulation will provide a major contribution. The same level of expectation exists with upcoming revisions of available certification and standardization schemes. Together with ongoing discussion and eventual regulatory actions on software liability, these initiatives may have the desired impact in the vulnerability “market”.