DNS DDoS Attack Protections
This Info Note reviews new DDoS attack patterns and the actions required to mitigate this threat.
- Published
- February 13, 2019
Introduction
According to a recent report, a new distributed-denial-of-service (DDoS) attack pattern dubbed ‘bit-and-piece’ has emerged, targeting communications service providers (CSPs) classified as a relevant entity, under the NIS directive. This report describes the new attack pattern as exploiting a large attack surface of ASN-level (autonomous system number) of CSPs. It is spreading small and fine-targeted traffic attacks across hundreds of IP-addresses to evade detection. In response to these events, multiple DNS software and service providers are planning to update their DNS software to prevent this type of threat. This update will allow CSPs to speed up DNS traffic and fight against this type of DDoS attacks. Stopping the implementation of DNS resolver workarounds still used by numerous DNS authoritative systems would be the significant mitigation measure for this threat. This Info Note reviews new DDoS attack patterns and the actions required to mitigate this threat.
Contextual Information
In January 2016, ENISA produced a paper describing DDoS attacks on DNS root servers on the realm of an attack affecting several servers around the world.
The DDoS threat and the recent attack patterns
The Nexusguard quarterly report, which is based on data from thousands of DDoS attacks around the world, showed that CSPs were targeted by 65.5% of DDoS attacks encountered in Q3 2018. Attackers were found to have contaminated diverse pools of IP-addresses across hundreds of IP prefixes (at least 527 Class C networks, according to Nexusguard findings) with very small-sized junk traffic. As a result, the year-over-year average attack size in the quarter fell by 82%.
"Perpetrators are using smaller, bit-and-piece methods to inject junk into legitimate traffic, causing attacks to bypass detection rather than sounding alarms with large, obvious attack spikes," says Juniman Kasman, chief technology officer for Nexusguard. "Diffused traffic can cause communications service providers to easily miss large-scale DDoS attacks in the making, which is why these organizations will need to share the load with the cloud at the network edge to minimize attack impact." said Juniman Kasman, Chief Technology Officer for Nexusguard.
The ‘bit-and-piece’ attacks observed, often leveraged on open domain name system (DNS) resolvers to launch what is commonly known as DNS Amplification. In these cases, a targeted IP-address receives only a small number of responses, leaving little or no trace. Furthermore, the researcher analysts believe that attackers conducted reconnaissance missions to map out the network landscape and identify the mission-critical IP ranges of targeted CSPs. By injecting bits and pieces of junk data into legitimate traffic - whose size easily fall below detection thresholds - they were able to operate unnoticed through traditional DDoS detection systems.
The response from the service providers
Multiple DNS software and service providers are planning to update their DNS software to prevent this type of attacks. The change will be performed by major resolver vendors (i.e., ISC, CZ NIC, NLNET Labs, PowerDNS) to their open source DNS resolvers. An update that will directly affect all authoritative servers that do not comply either with the original DNS standard from 1987 (RFC1035) or the newer EDNS standards from 1999 (RFC2671 and RFC6891).
According to DNS Flag Day initiative, the current DNS implementations are unnecessarily slow and inefficient because of efforts to accommodate a few DNS systems that are not in compliance with DNS standards established two decades ago. The entities registered on DNS Flag Day are now forcing DNS operations to include new mechanisms to protect against DDoS attacks. DNS software and service providers listed on this site agreed to remove non-compliant DNS implementations from their software or services. This deliberation, enforced since the beginning of this month, affects only sites operating non-compliant software.
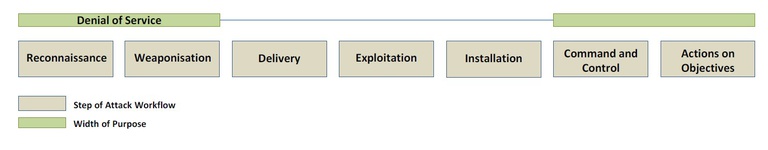
DDoS attack kill Chain
According to the 2018 ENISA Threat Landscape Report, the kill chain of this threat is as follows:
Recommendations
Recommendations for domain holders
Mitigating broadly distributed, small-sized attack traffic is more difficult at the CSP level, in comparison to the traditional volumetric attack method on a small number of targeted IPs. The convergence of polluted traffic that slips through the upstream internet service providers forms a massive traffic flow that easily exceeds the capacity of mitigation devices, leading to high latency at best and unavailability of service at worst.
- Domain owners are advised to check if hosted websites are ready for the DNS Flag Day deliberation. This will require validating if their hosted websites may become unreachable through updated resolvers.
- The dnsflagday.net website provides a diagnostic tool, which domain owners can check for DNS issues and receive advice on what steps they have to take to avoid being impacted.
Security measures for DDoS protection:
- Extra Bandwidth: An effective way to enhance DDoS protection is by increasing the bandwidth available on the web server. This allows the web server to handle sudden and unexpected surges in traffic. However, this is more of a buffer than a complete solution providing critical time to act before your resources are overwhelmed.
- Defend Network Perimeter:Enhance the network's defense perimeter by taking additional security measures such as:
- rate limiting the router to prevent web server becoming unresponsive to requests;
- dropping spoofed or malformed packages; and
- set lower SYN, ICMP, and UDP flood up thresholds.
- sinkholing all traffic: sinkholing an entire IP prefix may be a solution but is costly since it will also block access to a wide range of legitimate services.
Closing Remarks
CSPs are the first line of defense to prevent DDoS attacks. The ongoing evolution of DDoS methods suggests that CSPs need to enhance their network security posture and find more effective ways to protect their critical infrastructure and tenants. The continued discovery of new attack patterns should alert all parties involved to the importance of developing effective solutions. The notification in case of an incident is obligatory, as clearly defined in article 16 (4) of the NIS directive. The initiative promoted by DNS Flag Day initiative is an important step but will not entirely stop a threat that has made the top 15 since ENISA produced its first threat landscape report back in 2012.