An overview of the Wi-Fi WPA2 vulnerability
This note is meant to inform that a serious vulnerability affecting the Wi-Fi Protected Access II – WPA2 protocol has been discovered, presents the repercussions of a potential attack and offers basic security recommendations.
- Published
- October 19, 2017
What happened?
A security researcher discovered and disclosed a serious vulnerability affecting the Wi-Fi Protected Access II – WPA2 protocol, which is used by all modern, protected Wi-Fi enabled devices. The vulnerability enables an attacker to modify the protocol’s handshake, which can essentially lead to intercepting the internet traffic of a Wi-Fi network -and depending on the network configuration, it is also possible to inject and/or manipulate data, without owning or breaking its password security. The vulnerability is serious, has a very big attack surface but it also has its limitations: it cannot be performed remotely. It can be performed only when the attacker has physical proximity to the victim. There are already ways that people can protect themselves from the attack while waiting for security patches to be released for their devices. The severity of the issue should not be underestimated, albeit people should not panic as well. The biggest issue raised by this vulnerability -given its scale - is the fact that a vast majority of affected devices, e.g. smart devices, IoT, routers etc., might never receive a patch addressing the issue. This note provides an overview of the vulnerability, and some basic recommendations that can be followed whilst patches are rolled out by the various manufacturers/vendors.
Overview of the vulnerability and attack
The identified weakness is in the Wi-Fi standard itself, and not in individual products or implementations. Hence, according to the researcher, any correct implementation of WPA2 is likely affected (list of affected vendors). The attack against the vulnerability is dubbed KRACK (Key Reinstallation Attack) and enables an attacker to attack the 4-way handshake of the WPA2 protocol, i.e. the initiation of the WPA2 connection. This handshake takes place every time a client wants to join a WPA2 Wi-Fi protected network in order to confirm that the client and access point hold the correct credentials, i.e. Wi-Fi password, before the client joins the network. During the same 4-way handshake a fresh encryption key, which is used for encrypting subsequent traffic is established. By manipulating this 4-way handshake an attacker can trick a victim into reinstalling an already-in-use encryption key, while a key should only be installed and used once. Reinstalling an encryption key, forces two counters (known as “nonces”) used by the encryption protocol to reset and this enables an attack against the protocol e.g. replay, decrypt and/or forge packets.
A potential attacker who is in the physical proximity of a protected Wi-Fi network and carries out this attack, performs a man-in-the-middle attack. The attacker can essentially intercept/decrypt internet traffic without owning the credentials of the protected Wi-Fi network (therefore changing the Wi-Fi password won’t help). This attack can further be combined with downgrade attacks against SSL/TLS websites (that have not applied security measures against downgrade attacks) in order to turn an HTTPS[1] connection to HTTP and steal more sensitive information. The Key Reinstallation Attack is illustrated in the simplified figure below:
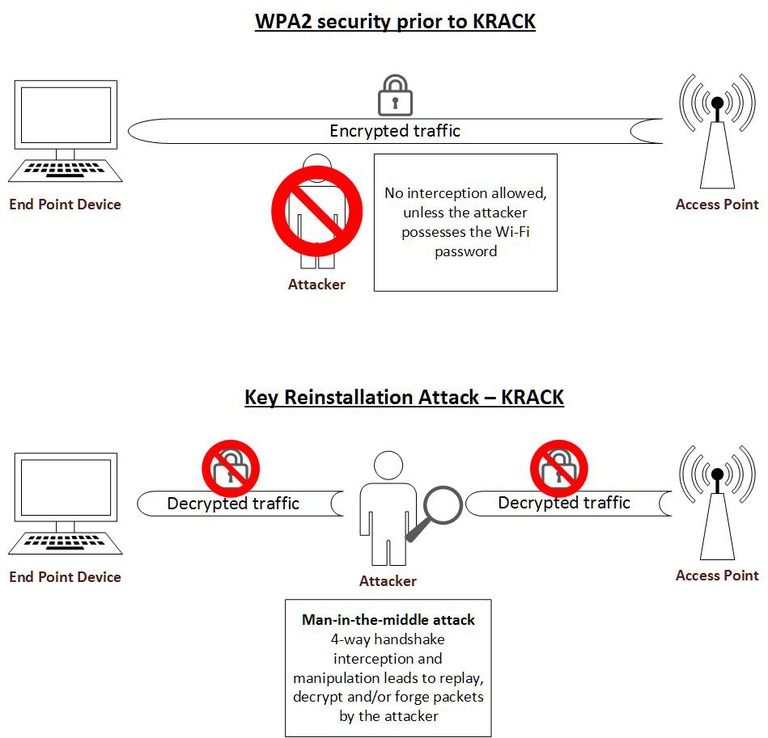
The attack works against personal and enterprise Wi-Fi networks, against the original WPA, WPA2, and even against networks that only use AES, i.e. pretty much most Wi-Fi network setups. For the technical interested audience, the researcher who discovered the vulnerability noted that the same key reinstallation technique can also be used to attack the group key, PeerKey, TDLS, and fast BSS transition handshakes as well.
The researcher describes the vulnerability in the paper called “Key Reinstallation Attacks: Forcing Nonce Reuse in WPA2”, which is a highly technical paper for those interested in the details of the attack. Additionally, the researcher provided a video with a proof-of-concept attack against an Android smartphone.
Lines to take
- Despite the fact that vulnerability is present in the Wi-Fi standard and thus affects a very large number of devices, do not panic!
- The WPA2 vulnerability is severe and provides a big attack surface but it can only be exploited within the physical proximity of the target Wi-Fi network and not remotely through the Internet, which reduces its impact.
- WPA2 is only one of the available layers of security impacted. Keep in mind that properly configured websites, e.g. usually banks, e-mail providers, social media etc. that use TLS (HTTPS) are still protected from such an attack.
- There is no evidence that the vulnerability has been exploited in the wild and it is uncertain of how easily this vulnerability can be exploited.
- WPA2 is still a more secure solution compared to WEP -the previous Wi-Fi protocol. Hence, switching to an older -trivially exploitable- protocol, is highly discouraged. It is better to continue using WPA2 when using Wi-Fi.
- Avoiding WPA2 protected Wi-Fi networks all together is highly unrealistic. Thus, in such cases people should be pragmatic, apply available security measures or use 4G mobile internet connections, while waiting for manufacturers to prepare and push patches for their devices.
- The issue can be resolved with software/firmware updates. Check with the manufacturer/vendor for each of your Wi-Fi enabled devices and apply patches as soon as they become available. Manufacturer readiness on such issues should be a weighting factor for purchasing technological devices. Home users who obtain their routers from their broadband providers should contact their provider and check whether there is a patch available for their equipment and ask for installation instructions.
- Whenever possible use a 4G mobile internet connection instead of a Wi-Fi connection.
- While waiting for patches, you may treat all Wi-Fi networks like public, open and insecure networks. Therefore, apply security measures on different layers. This is an essential rule in security and quite effective in this case as well. Namely:
- Use only HTTPS websites. Refrain from using simple HTTP websites and sharing personal information through them. Consider using a browser extension like HTTPS Everywhere, which forces any site that supports HTTPS connections to encrypt your communications with that website by default
- Use a trusted Virtual Private Network – VPN provider. VPNs establish an encrypted tunnel between an endpoint and the trusted provider, protecting internet traffic routed through untrusted networks. This means that by using a VPN, an attacker that carries out KRACK cannot intercept the user’s traffic. Keep in mind that choosing a trusted VPN provider is crucial when using a commercial VPN solution.
- Organisations should separate their wireless networks from their enterprise, wired networks.
Relevant ENISA actions
In the last years ENISA has invested a lot of resources in the Telecom area. Since 2011 a considerable number of guidelines/studies have been produced and more than 700 incidents have been collected and analysed. All those were made possible through the support of the Art. 13a Expert Group, a dedicated security group made of national authorities across EU.
In the case of the WPA2 vulnerability, an ad-hoc cooperation initiative started within the group, and the results can be summarised at this point as follows:
- All Member States regulatory authorities are aware of the seriousness of the situation; they have issued warnings, alerts or other relevant information that include also recommendations for end users;
- A dialog has been established between authorities and telecommunication providers (ISP) at national level in order to identify specific risks within each context (e.g. main types of routers used in each country, if patches have been released etc.) and actions taken by providers.
Closing Remarks
Every time a vulnerability affects the security of a network or a cryptographic protocol a wide range of devices or services are potentially put at risk. In such cases it is useful not to panic and carefully assess the theoretical and practical risk of the vulnerability. Having said that, it is advised to also take into account the available security measures, in order to determine the vulnerability’s potential impact. One of the main issues and challenges raised by this vulnerability is the state of readiness of manufacturers to respond to such incidents, prepare, push patches to their products in a timely manner, and not leave their products vulnerable. As internet connected devices are becoming ubiquitous, it is essential to work on keeping this ecosystem protected since we have already experienced security incidents that aim to undermine the state of cyber security.
[1] An HTTPS connection ensures that all data exchanged between a client and a server, e.g. a user’s pc and a website, are encrypted and only these two parties are able to decrypt the encrypted traffic. This means that it is safe for people to send sensitive information over HTTPs connections, e.g. credit card information, personal information etc. This is NOT true for simple HTTP connections. Sensitive data should NOT be sent over simple HTTP connections because an attacker might intercept and steal it. It is easy to ensure that you use a secure HTTPS connection by spotting a) the "https://" prefix in the address bar of the browser b) the padlock displayed in the address bar of the browser. This is illustrated in the picture below: