Publication date:December 6, 2013
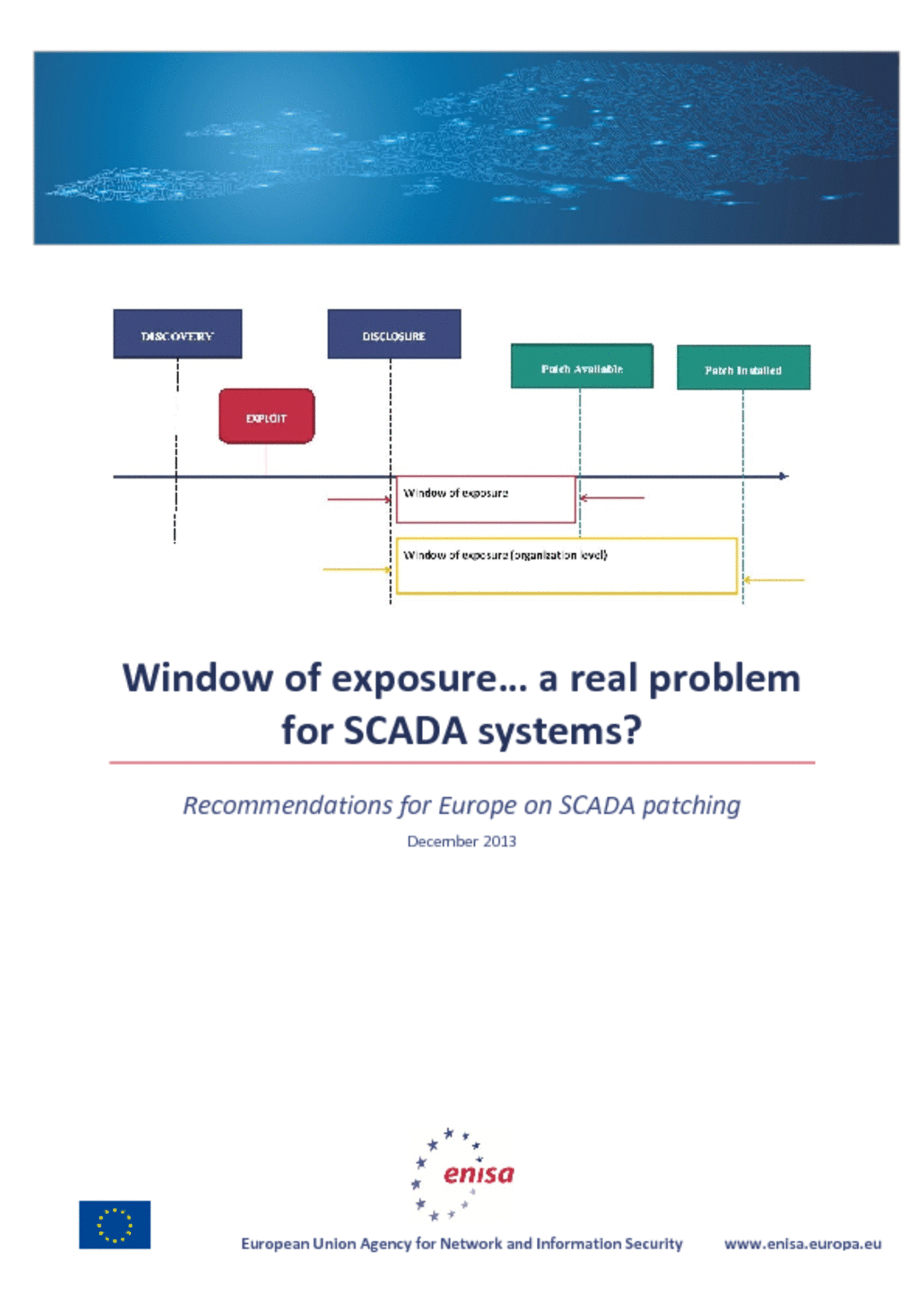
Much of Europe’s critical infrastructure which resides in sectors such as energy, transportation,water supply is largely managed and controlled by SCADA (Supervisory Control and Data Acquisition) systems, a subgroup of Industrial Control Systems (ICS). In the last decade SCADA technology has passed through a transformation, from isolated and proprietary systems into open architectures and standard technologies that are highly interconnected with other corporate networks and the Internet. A consequence of this transformation is the increased vulnerability to outside attacks. One way to enhance the security of SCADA is through the application of patches. Ideally an organization would deploy patches as soon as they come available, however this is often not possible because of the complexity of the process in which SCADA systems are incorporated and because the systems often need to be operable at any given moment. Furthermore patches need to be tested thoroughly before they can be applied to production environment, which can take days or even weeks, during which a system is vulnerable. Alternative controls should be used during the WINDOW OF EXPOSURE for preventing a vulnerability to be exploited. For instance, when a webserver vulnerability has been discovered the organization could, if possible, block unwanted traffic to the webserver or disable the webserver all together.
Search related content with: Critical Information Infrastructure Protection (CIIP)