BC/RM Interfaces
Corporate Governance is concerned with improving the performance of companies for the benefit of shareholders, stakeholders and economic growth. It focuses on the conduct of, and relationships among, the Board of Directors, Managers and Shareholders. It generally refers to the processes by which organisations are directed, controlled and held to account. It encompasses authority, accountability, stewardship, leadership, direction and control exercised within the organisation [HB 254-2005].
The Australian Stock Exchange has developed ten core principles which underlie sound corporate governance, one of which is recognising and managing risk. According to HB 254-2005, the integration of a Risk Management processes into an organisation’s corporate governance framework has the following advantages:
- More effective strategic and operational planning
- Greater confidence in achieving planned operational and strategic objectives
- Greater confidence in the decision-making process
- Greater stakeholder confidence and enhanced capital-raising
- Director protection
- Enhanced operational resilience (and continuity)
Risk is present in all decisions and activities undertaken by organisations and a number of these will present continuity issues. The approach to managing these continuity risks is twofold:
1 Pro-actively manage the risk, as part of the organisation’s Risk Management process on an ongoing basis to lessen the likelihood or impact of an incident. The Business Continuity process itself can highlight further risks, which will themselves become part of the Risk Management process.
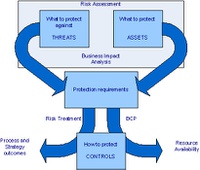 2 Implement a Business Continuity Management process to treat residual risk. Business Continuity Management should be conducted as one of the required outcomes of the Risk Management programme. Both BS 25999-1 and the Draft for Public Comment BS 31100 – Code of Practice for Risk Management [BS 31100 DPC] – states that Business Continuity is one of the ways of modifying risk to lessen the impact if the risk occurs; especially in cases where avoiding, transferring or accepting the risk are not appropriate risk treatments. This could be considered a reactive method of managing risk.
2 Implement a Business Continuity Management process to treat residual risk. Business Continuity Management should be conducted as one of the required outcomes of the Risk Management programme. Both BS 25999-1 and the Draft for Public Comment BS 31100 – Code of Practice for Risk Management [BS 31100 DPC] – states that Business Continuity is one of the ways of modifying risk to lessen the impact if the risk occurs; especially in cases where avoiding, transferring or accepting the risk are not appropriate risk treatments. This could be considered a reactive method of managing risk.
ISO 27001:2005 calls for Business Continuity Management, as a method of risk treatment, to be considered as a measure to counteract interruptions to business activities and to protect critical business processes from the effect of major failures of information systems or disaster as well as to ensure their timely resumption.
A further comparison of Risk Management and Business Continuity Management is given in the following table.
| Risk Management | Business Continuity Management | |
|---|---|---|
| Key Method | Risk Analysis | Business Impact Analysis |
| Key Parameters | Impact and Probability | Availability and Impact |
| Type of incident | All types of events | Events causing significant business disruption |
| Size of events | All events affecting the organisation | Those threatening availability of organisation's core processes |
| Scope | Focus primarily on management of risks to core business objectives, to prevent or reduce incidents | Focus mainly on incident management and recovery of critical business processes following an incident |
| Intensity | All, from gradual to sudden | Sudden or rapid events (although response may also be appropriate if a creeping incident suddenly becomes severe) |
Business Continuity Management is concerned with managing risks to ensure that at all times an organisation can continue operating at least to a pre-determined minimum level. The BCM process involves reducing the risk to an acceptable level and planning for the recovery of business processes should a risk materialise and a disruption to the business occur.
Disaster Recovery Planning is concerned with the actual technical recovery of the IT components and details the procedures to be used to restore the IT components following a failure. As the plan is devised by ICT without the knowledge and understanding of business units as to their IT requirements, it is an orderly but non-prioritised recovery process. The Disaster Recovery Plan will not be discussed in this document, but its existence is mentioned for completeness.
Information Technology Service Continuity Management (ITSCM) ensures that information technology technical and services facilities (including computer systems, networks, applications, telecommunications, technical support and service desk – referred to as IT components throughout the remainder of this document) can be recovered within required and agreed business timescales. ITSC Management should be part of the overall BCP and not dealt with in isolation (PAS 77: 2006). The major difference between DR planning and ITSCM is that the user requirements drive ITSCM - their recovery time objectives and agreed recovery sequence (taken from dependencies and RTO for applications). This enhances the service as it focuses the recovery effort on the Business Continuity requirements and reduces disruption to the critical processes.
Definitions of the various risk-related disciplines are given in the following table.
| Risk discipline | Description |
|---|---|
| Corporate Governance | The system by which entities are directed and controlled [HB 254-2005] |
| Risk Management | Process of enhancing an organisation's likelihood of success in achieving its objectives [HB 254-2005], [BS 31100 DPC] |
| IT Risk Management | The process, distinct from Risk Assessment, of weighing policy alternatives for the safeguard of data assets and IT systems in consultation with interested parties, considering Risk Assessment and other legitimate factors, and selecting appropriate prevention and control options. (ENISA) |
| Business Continuity Management | BCM assures the availability of processes and resources in order to ensure the continued achievement of critical objectives [HB 293-2006] |
| IT Service Continuity Management | Supports the overall Business Continuity Management process by ensuring that the required information technology components can be recovered within required, and agreed, business timescales and in the agreed order of priority, from data extracted from the BIAs. The underlying recovery procedures can then be prioritised to effect recovery in a timely fashion [PAS 77] |
| Disaster Recovery Planning | Disaster Recovery Planning refers to an IT-focused plan designed to restore operability of the target system, application, or computer facility. The scope may overlap that of an IT Service Continuity Plan; however, the DR Plan is narrower in scope as it does not address the requirements of the business (based on [NIST]) |
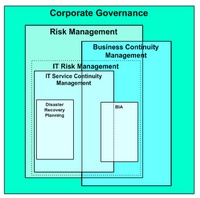 The relationships among Corporate Governance, Risk Management, Business Continuity Management, IT Service Continuity Management and Disaster Recovery Planning are complex since some can exist without the others. The following figure tries to explain the relationships, should they co-exist.
The relationships among Corporate Governance, Risk Management, Business Continuity Management, IT Service Continuity Management and Disaster Recovery Planning are complex since some can exist without the others. The following figure tries to explain the relationships, should they co-exist.
BCM overlaps with Risk Management, and one of the areas of convergence is Business Impact Analysis. If ITSCM is in place, it utilises some of BIA’s information in order to achieve Continuity Management and align it with the needs of the business. That is the only information which BCM and ITSCM have in common. ITSCM uses this information in order to prioritise the plans developed through DR Planning.
If ITSCM does not exist within the organisation then DR Planning is the pro-active risk mitigation function of Risk Management and although it impacts BCM and can be invoked by a BCM event it is not part of BC. Similarly, ITSCM can exist without BCM but requires a subset of BIA information so the Business must conduct BIAs in order to ascertain the necessary information. If there are no DR Plans then these must also be developed. DR Planning is an essential part of ITSCM. Although it may not exist when originally developed it must be in operative if ITSCM is to be considered complete. In a similar way, BCM cannot exist without BIA information.
Risk Management and Business Continuity need to be considered as an integrated whole together with IT Service Continuity and Information Security. The successful implementation of a robust Business Continuity Plan is dependent upon having a tried and tested ITSC Plan in place which improves the technological resilience of the organisation. This requires the presence of procedures for restoration should any part of the IT infrastructure fail.
Not only should the Business Continuity Plan consider the IT requirements of the business processes within the organisation, and how ICT will organise themselves to restore services to meet the business requirements following an incident, but the Business Continuity Plan must consider the information requirements. BS 7799-3 [BS 7799-3] states that one of the most valuable assets of an organisation is its information which needs to be protected whatever its form. Information assets, which can be databases, contracts, user manuals and training materials, or other types of information, are stored on or used by other assets and these may be defined as:
- Processes and services
- Software
- Physical items
- Personnel
Information Security (IS) must be able to recover its own processes following an incident in order to be able to restore the business processes’ information requirements. Interdependencies will exist between ICT and IS and the two will need to work together to ensure an integrated approach which meets business needs.
There are other security disciplines related to Business Continuity which are described in the following paragraphs and illustrated bellow.
Emergency Planning: Emergency planning is a process resulting in a set of agreed procedures to prevent, reduce, control, mitigate and take other actions in the event of a civil emergency which impacts the organisation [BS 25999-1].
Incident Response: Incident response is the immediate response to an incident usually within the first few hours of occurrence. It is an important phase in which control should be gained of the incident, the impact assessed, personnel made safe and key communications made to staff, public, stakeholders and the media. If control is not gained at this stage it is extremely difficult to implement effective incident management thereafter (Glen Abbot).
Incident Management: Incident Management is the process of taking central command and control of an incident which threatens the operations, staff, stakeholders or reputation of an organisation. The incident management team ensures that staff are able to restart their critical processes and communications are made internally and externally (Glen Abbot).