Phishing on the rise
This note provides an overview of phishing tactics, a visualisation of how phishing interconnects with other cyber-threats, and basic security recommendations against phishing.
- Published
- October 12, 2017
Introduction
According to recent reports, in 2017, phishing campaigns have increased both in volume and sophistication. Phishing is highly used as the first step in cyber-attacks and is amongst the most prominent causes of data breaches and security incidents for both targeted and opportunistic attacks. This note is based on the results of the aforementioned reports. It provides an overview of phishing tactics, a visualisation of how phishing interconnects with other cyber-threats, and basic security recommendations against phishing.
Phishing tactics
Targeted attacks
Originally, phishing attacks were being deployed through massive spam campaigns that indiscreetly targeted people. The goal was to trick a sufficient number of people to click on a malicious link or download a malicious attachment and ultimately harvest their credentials and install malware (or exfiltrate data) respectively.
Nowadays, the goal remains the same but phishing attacks have become more targeted and sophisticated. “Spear-phishing” is used to specifically target an individual or group of people. Spear-phishing is a phishing attack that is highly tailored to the target (usually based on all sorts of gathered public information, e.g. social media), which makes it difficult to determine its malicious nature. In a previous note “Business e-mail compromise – BEC” was also described. This phishing technique (also known as “whaling”) refers to spear-phishing attacks against C-level executives, usually with the aim to steal money from their organisations or to conduct cyber espionage.
Spam and phishing are two cyber-threats that go hand in hand, while botnets are usually employed to deliver them. It was recently reported that there was an increase in targeted attacks where e-mails were masked as business correspondence. Spammers used details of real companies, e.g. e-mail subject message, logos, e-mail signatures etc., in order to impersonate them and “phish” their targets -reportedly the B2B sector. Such targeted attacks usually aim to have financial gain; either by delivering ransomware (therefore asking for a ransom in order to decrypt valuable corporate data), either delivering spyware to steal financial information, or to compromise e-mail accounts of company employees and perform various types of internal phishing and BEC attacks. Moreover, such attacks have targeted industrial companies from the metallurgy, electric power, construction, engineering and other sectors, in which cases the risk of unauthorised access and control of corporate networks and industrial equipment rises.
Phishing delivering malware
As previously noted, phishing is widely used as the first step of a cyber-attack (initial infection vector) that aims to give an attacker foothold on a target system. Phishing usually delivers a booby-trapped link or attachment (most often in the form of a document), which upon access/execution infects the target system with malware e.g. ransomware, banking Trojans, backdoors etc. More precisely, a survey showed that in 2017, 74% of the cyber-threats entered a system as an e-mail attachment or link.
Imposed urgency and compelling phishing attacks
Phishing’s success often relies on the sense of urgency it imposes to the victim. Phishing e-mails usually urge the victim to take action upon something within a limited span, e.g. act upon an alleged data breach, act upon the delivery of a product, act upon a password expiration reminder etc. This phishing approach aims at the natural human tendency to take action, which might oversee the signs of abuse.
Technology support scams are similar attacks that aim to trick the users to download malicious software by using fake and deceiving system and error lookalike messages. Additionally, phishing attacks through malicious mobile applications that fake system pop-up notifications -in their effort to steal user credentials- are also considered an upcoming threat.
In one case of a phishing attack, the threat actor sent fake notifications allegedly originating from software vendors, urging potential victims to update the respective software due to their systems being supposedly infected by WannaCry. The link to the alleged update led to a phishing page hoping that victims would panic and access it. It is known that after major events, e.g. cyber-incidents, physical catastrophes, political/social events, etc., cyber criminals grasp the opportunity to initiate new spam and phishing campaigns.
The sense of urgency imposed by phishing attacks is tied to quite compelling e-mails and fake websites that cleverly impersonate legitimate entities and third party websites respectively. Often, these websites may look identical both content-wise and in terms of the domain name –which is found at the URL address bar of every browser. More precisely, phishers often use non-Latin characters that look very similar to Latin letters but they can easily go unnoticed to the untrained eye.
Detection evasion
In the past, spam campaigns used one or just a few phishing websites for the entire phishing campaign, which made it feasible for defenders to block the malicious domains. According to the data of a recent report, phishing campaigns rely on multiple and short-lived websites per campaign. This means that the life-cycle of a phishing campaign has become significantly smaller (in the magnitude of a few hours) and that traditional anti-phishing techniques, e.g. block lists, do not suffice against the ever increasing number of malicious domains.
In several instances, phishing e-mails were spotted of being accompanied with password-protected archives as attachments. This tactic served a dual purpose. They created a false sense of security to the victims, implying that legitimate confidential data were exchanged and hence it was reasonable for the archives to be password-protected. Additionally, they evaded antivirus solutions since such files have to be extracted before they can be scanned by antivirus software. Phishers are always in the look for new techniques that will help them avoid detection. One more is the abuse of legitimate services.
Abuse of legitimate services
Aside from direct e-mail phishing attacks, phishers leverage social media and legitimate websites too. Threat actors are in a constant research for ingenious ways of abuse/delivering phishing. As reported, “one of the phishers’ tricks is to place pages of popular organizations on domains belonging to other popular organizations” in their effort to induce credibility to their phishing attacks. This makes the detection and mitigation even more difficult since legitimate sites are also used in the process. Threat actors mostly focus on involving popular websites in their phishing campaigns, hoping that they will have higher chances of success.
Phishing and cyber-threat context
According to recent data “an average of 1.385 million unique phishing sites are created each month with an astonishing high of 2.3 million in May of 2017”. Phishing, targets a wide range of sectors, e.g. Banks, transport companies, global internet portals, social networks etc. The figures suggest that phishing is effective and thus it is highly used by threat actors. Furthermore, phishing as a service is also used by cybercriminals and uses full-fledged frameworks to perform phishing attacks. As noted by ENISA’s Threat landscape and depicted in the figure below, phishing is related to major cyber threats, e.g. spam, botnets, malware and data breaches. The various cyber threats that relate to a phishing attack become apparent when different examples of phishing attacks are analysed. The figure below shows the steps involved in different phishing attacks.
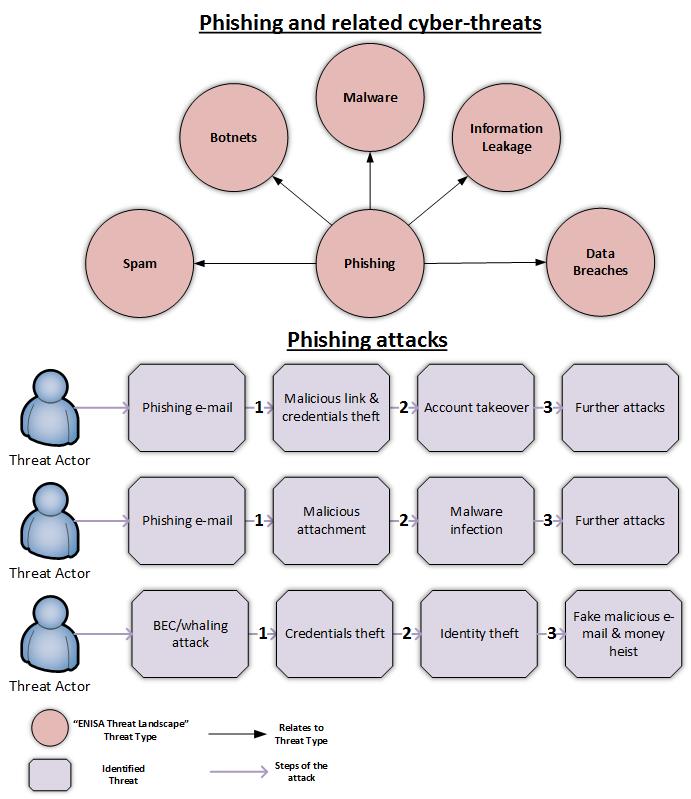
Providing cyber-threat contextual information to phishing attacks highlights the interconnection between the different cyber-threats and the dynamic nature of the threat landscape. Additionally, based on the identified related threats more targeted security recommendations can be provided by ENISA’s Threat Landscape.
Recommendations
The following security recommendations apply against phishing attacks:
- Organisations should educate their staff to identify fake and malicious e-mails and stay alerted. They should also internally launch simulated phishing attacks to test both their infrastructure and the responsiveness of their staff.
- Organisations should use specialised security e-mail gateways for filtering spam, which is heavily related to phishing campaigns
- Do not click on links or download attachments if you are not absolutely confident about the source of an e-mail
- Do not click on random links and especially short-links found in social media
- Avoid over-sharing personal information in social media, e.g. time of absence from office or home, flight information etc. as they are actively used by threat actors to collect information about their targets
- Check the domain name of the websites you visit for typos, especially for sensitive websites, e.g. bank websites. Threat actors usually register fake domains that look similar to legitimate ones and use them to “phish” their targets. Looking only for an https connection is not enough
- Do not click on “enable content” (which enables macros) in Microsoft Office documents. Macros are leveraged to download and install malware
- Enable two factor authentication whenever applicable. Two factor-authentication can prevent account takeover
- Use a strong and unique password for every online service. Re-using the same password in various services is a serious security issue and should be avoided at all times. Using strong and unique credentials in every online service limits the risk of a potential account takeover to the affected service only
- In case of wiring money to an account, double check the bank information of the recipient through a different medium. Unencrypted and unsigned e-mails should not be trusted, especially for sensitive use-cases like these
- Consider applying security solutions that use machine learning techniques to identify phishing sites in real time
Conclusion
Phishing is a quite pervasive attack because it uses social engineering to attack the weakest link in security, the human element. Hence, phishing is not going away anytime soon. Instead, phishing is becoming more and more sophisticated and targeted, which makes its detection more difficult. As in most cases in security a multilayer security approach is suited against phishing. Moreover, new solutions that involve machine learning should be considered in order to assist and enhance traditional security measures.