Cybercriminals are increasing efficiency with coordinated attacks
This Info Note reviews new forms of collaboration between cybercriminals and identifies an approach to mitigate the risks of coordinated attacks.
- Published
- January 22, 2019
Introduction
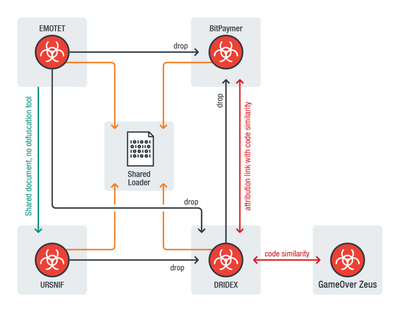
Recent research revealed that threat groups might be combining efforts to develop more sophisticated attack vectors to increase the efficiency of their attacks. The comparison conducted to four malware families used by different threat actor groups suggests that these might be sharing information and resources. The researcher identified a connection between EMOTET, URSNIF, DRIDEX, and BitPaymer from the open source information and the loaders of the samples analysed. Evidence show that malware developers are trying to increase the sophistication and efficiency of their tools by reducing the deployment time through the distribution of tasks among multiple criminal groups and re-using capabilities from existing tools. This collaborative model includes the distribution of loaders and decryptors, aiming at reducing the workload during an attack. This Info Note reviews new forms of collaboration between cybercriminals and identifies an approach to mitigate the risks of coordinated attacks.
Contextual Information
A security researcher identified that cybercriminals behind the recent deployment of well-known banking malware might have been sharing code to collaborate with trusted, highly-skilled cybercriminal groups. The researcher also argues that these cybercriminal groups are engaged in an ongoing relationship/collaboration.
From the analysis of the disassembled malware packages, the researcher identified that the Trojans EMOTET, URSNIF, DRIDEX, and BitPaymer present similar characteristics. Despite the small differences in the arithmetic operations’ instructions, “the four payload decryption procedures were identical in data structures’ overview of the way they decrypted the actual PE payloads.” the researcher explained.
Figure 1 - Connections of EMOTET, DRIDEX, URSNIF and BitPaymer (TrendMicro 2019)
Description of the malware analysed
W32/URSNIF, GOZI-ISFB – A well-known banking trojan recognized for its adaptive behaviour. This malware steals system information, email data, online banking account credentials, monitors traffic, features a keylogger, and steals credentials stored in browsers and applications. Known URSNIF variants include backdoors (BKDR_URSNIF.SM), spyware (TSPY_URSNIF.YNJ), and file infectors (PE_URSNIF.A-O).
DRIDEX - Another banking trojan that targets banking and financial institutions, the cybercriminals behind it use various methods and techniques to steal personal information and credentials through malicious attachments and HTML injections. DRIDEX evolved from CRIDEX, GameOver Zeus and ZBOT, and proved to be resilient even after it was momentarily taken down in 2015.
EMOTET- A Trojan recognized for its modular architecture and ability to spread itself quickly and effectively. While it’s technically considered a banking trojan, Emotet is more commonly used as a dropper for other types of malware, such as TrickBot and Zeus Panda Banker, among others. Previous research has shown similarities in the obfuscation techniques used by both Emotet and Ursnif/Gozi-ISFB.
BitPaymer - This ransomware was used to target medical institutions via remote desktop protocol (RDP) and email-related techniques, shutting down routine services briefly for a ransom. Security researchers later published evidence that not only was DRIDEX dropping BitPaymer, but that it also came from the same cybercriminal group. BitPaymer is operated by the same group distributing Dridex and which was also behind the Locky ransomware.
How threat groups increase efficiency and sophistication with collaboration
In recent years, efficiency and sophistication have been highly desirable characteristics in malware development.
Malware developers have been producing software by using open-source tools created by other developers and distributing tasks among multiple criminal groups. By maintaining their own obfuscation or evasion procedures, developers collaborate on common elements such as loaders and decryptors to reduce the total workload.
Another trend is the increase in sophistication. Collaborating, criminal groups can reduce the number of coding errors via peer-review checks and avoid duplicating defeated attack vectors by leveraging from previous experiences. Besides, the inclusion of multiple capabilities from different tools provides powerful out-of-the-box packages: Ursnif distributors can more easily compromise networks with BitPaymer attacks and Emotet loaders.
Recommendations
A back-to-basics approach is recommended when protecting against malware threats that includes (but not limited to): ensure that all end-point security software is up to date, keep software fully patched, train users to avoid being targeted by spam and phishing attacks, and conduct regular vulnerability assessments and penetration tests to withstand cyberattacks.
Additional recommendations for Cybersecurity Operations and Cyberthreat Intelligence Teams:
- Cybersecurity operations team to implement honeypots or other means to capture and analyse techniques used in the different malware families.
- Cybersecurity operations team to use a malware sandbox to automate the process of malware analysis:
- Detect malware techniques or behaviours (process injection, decompression of executable modules in memory, extraction of executable modules or shellcode in memory, etc.) from its initial run on a sample.
- Extract the malware payload and possibly its configuration from any further run with a particular package;
- Use malware signatures and API hooks to trigger detection and configuration parsing of the malware;
- Use a software debugger to control the malware execution and dump the memory containing code or configuration data.
- The Cybersecurity Operations team to register and classify all the information obtained from the analysis in the corporate Security Information and Event Management (SIEM).
- The CTI team to analyse the threat using the information available in the SIEM and external sources. Populate the cyber kill-chain method to identify the complete intrusion activity and enrich the analysis using the information available in the corporate SIEM about each malware capability and behaviour.
- The CTI team to identify specific countermeasures for each malware family, capability, behaviour across the different stages of the cyber kill-chain.
- The CTI team to prepare a cybersecurity intelligence report and disseminate it with its stakeholders. The report/threat information should be prepared and formatted considering each stakeholder intelligence requirements and expectations.
The organizers of the RSA Conference recently announced that United States (US) National Security Agency (NSA) is planning to showcase a tool that allows the reverse engineering of malware. The tool dubbed GHIDRA, used for almost a decade by the US government to investigate suspicious software, will become available to the public during this year conference through the Agency’s Github account. Disassembling and debugging software can be a powerful tool for security professionals to analyse suspicious software activity in a system or network or malware samples caught in a honeypot.
Closing Remarks
While end-users, smaller size and less resourced organizations continue to really on traditional cybersecurity defense systems such as anti-virus, larger organizations are looking into more sophisticated solutions to have a better understanding about threats and ultimately increase their detection and protection mechanisms. Malware honeypots, honeytokens, and honeytraps are useful resources to detect and analyse malware by attracting attacks on itself in a separate environment. From having a better understanding of how a particular malware behaves, defenders are capable of improving their defence systems and train users based on real scenarios. Another important use of this knowledge is to share it outside the organization and contribute to others threat assessments. With adversaries exploring new ways to increase the efficiency of their attacks though collaboration and complexity in tools, it’s time for defenders to apply the same thought process.