How to map the Cybersecurity Threat Landscape? Follow the ENISA 6-step Methodology
The cybersecurity threat landscape methodology developed by the European Union Agency for Cybersecurity (ENISA) aims at promoting consistent and transparent threat intelligence sharing across the European Union.
Published on July 06, 2022

With a cyber threat landscape in constant evolution, the need for updated and accurate information on the current situation is growing and this a key element for assessing relevant risks.
This is why ENISA releases today an open and transparent framework to support the development of threat landscapes.
The ENISA methodology aims to provide a baseline for the transparent and systematic delivery of horizontal, thematic and sectorial cybersecurity threat landscapes (CTL) thanks to a systematic and transparent process for data collection and analysis.
Who can benefit from this new methodology?
This new methodology is made available to ENISA’s stakeholders and to other interested parties who wish to generate their own cyber threat landscapes. Adopting and/or adapting the proposed new CTL framework will enhance their ability to build situational awareness, to monitor and to tackle existing and potential threats.
ENISA will also be using this new methodology to deliver an enhanced annual ENISA Threat Landscape (ETL). It will also be used to generate technical or sectorial threat landscapes.
How does the methodology work?
The framework is based on the different elements considered in the performance of the cybersecurity threat landscape analysis. It therefore includes the identification and definition of the process, methods and tools used as well as the stakeholders involved.
Building on the existing modus operandi, this methodology provides directions on the following:
- defining components and contents of each of the different types of CTL;
- assessing the target audience for each type of CTL to be performed;
- how data sources are collected;
- how data is analysed;
- how data is to be disseminated;
- how feedback is to be collected and analysed.
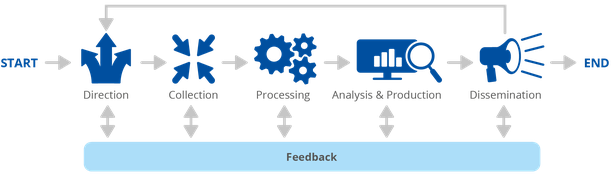
The ENISA methodology consists of six main steps with feedback foreseen and associated to each of these steps:
- Direction;
- Collection;
- Processing;
- Analysis and production;
- Dissemination;
- Feedback
This CTL methodology has been validated by the ENISA ad-hoc working group on the Cybersecurity Threat Landscape (CTL WG). The group consists of European and international experts from both public and private sector entities.
ENISA’s work on the Cybersecurity Threat Landscape
ENISA is constantly looking for ways to gather feedback and to continually improve and update the methodology applied to the performance of cybersecurity threat landscapes. Please feel free to reach out to [email protected] with suggestions.
The ENISA CTL methodology intends to provide a high-level overview of how to produce a CTL. This methodology is therefore meant to evolve in time according to any possible new developments in the process. The ongoing research and work ENISA performs in the area is meant to ensure the transparency and trust in the contents of the reports produced.
Target audience
- European Commission and European Member States policy makers (including but not limited to European Union Institutions (EUIs);
- EU institutions, bodies and Agencies (EUIBAs);
- Cybersecurity experts, industry, vendors, solution providers, SMEs;
- Member States and national authorities (e.g. Cybersecurity Authorities);
Further information
- ENISA Cyber Threat Landscape Methodology 2022
- ENISA Threat Landscape 2021
- Threat Landscape for Supply Chain Attacks
- Ad-Hoc Working Group on Cyber Threat Landscapes
Contact
- For questions related to the press and interviews, please contact press(at)enisa.europa.eu
Stay updated - subscribe to RSS feeds of both ENISA news items & press releases!
News items:
http://www.enisa.europa.eu/media/news-items/news-wires/RSS
PRs:
http://www.enisa.europa.eu/media/press-releases/press-releases/RSS